SAML overview
SAML is an XML-based data format for exchanging user authentication between the customer identity provider (IdP) and WFO as the Service Provider (SP), or Relying Party (RP). Similar to the Kerberos ticket exchange in Windows Active Directory (SSO), SAML SSO works by transferring the user's identity from the IdP to SP. This is done through an exchange of digitally signed XML documents (SAML assertion).
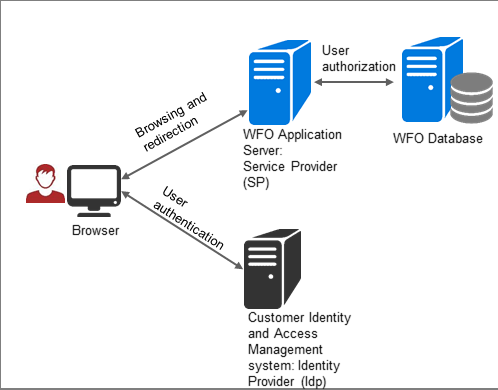
Authentication
User authentication flow can start by browsing to WFO system (SP-initiated flow) or by browsing to the customer IdP portal (IdP-initiated flow).
In both cases, the IdP authenticates the user and sends a digitally signed SAML assertion to WFO with the user's identity. WFO trusts the SAML assertion provided by the IdP and logs the user in.
Authorization
Once the IdP authenticates a user, WFO authorizes the user according to their specific rights and permissions, as defined in the user management application (saved in the system database).
In WFO, each user is assigned one or more roles, where each role contains a set of privileges. A role and its privileges allow the user to view certain pages and to perform certain functions within the system.
SP-initiated sequence flow
-
The user sends a /wfo/control/signin request to WFO Application Server (specifically the WebLogic service). Once prompted, the user enters a user name.
-
Based on the user name, the system identifies the user as a SAML account. The WFO Application Server delegates the authentication to the IdP, by redirecting the browser to the IdP with a SAML request.
-
The browser sends the SAML request to the customer IdP.
-
The customer IdP authenticates the user identity details in the SAML request. If authenticated, redirects the browser back to WFO with SAML response (signed SAML assertion).
-
The browser sends the SAML response with the authenticated user identity details to the WFO Application Server.
-
The WebLogic service in the WFO Application Server validates the SAML response, extracts the authenticated user details from the response, and grants the user with access rights to WFO (user authorization).
IdP-initiated sequence flow
-
Using a web browser, a user signs in to the customer IdP portal. If signed-in, the user selects a link to WFO.
-
The customer IdP provides a SAML response with the authenticated user identity details and redirects the user to WFO.
-
The browser sends the SAML response with the authenticated user identity details to the WFO Application Server.
-
The WebLogic service in the WFO Application Server validates the SAML response, extracts the authenticated user details from the response, and grants the user with access rights to WFO (user authorization).